CTF: WinjaCTF | Nullcon Goa 2023 - OSINT

Hey amigos, I participated in WinjaCTF Nullcon Goa 2023 online and solved some OSINT and web challenges. However, I could only solve two challenges in the OSINT category. In this article, I’m going to demonstrate how I solved these OSINT challenges.
Memento
Pts: 100
Megan, who tends to be forgetful, embarked on a journey to an unfamiliar destination. While capturing memories through photographs, she encountered an unfortunate incident where one of her pictures became distorted. Now, she is eager to share this particular picture with a friend, but alas, she has completely forgotten the name of the place she visited. Would you be kind enough to assist her in recalling the forgotten location?
Flag Format is flag{NAME_OF_THE_PLACE}. All words in Caps seperated by underscore.
This is an easy challenge. download the given file and open it.
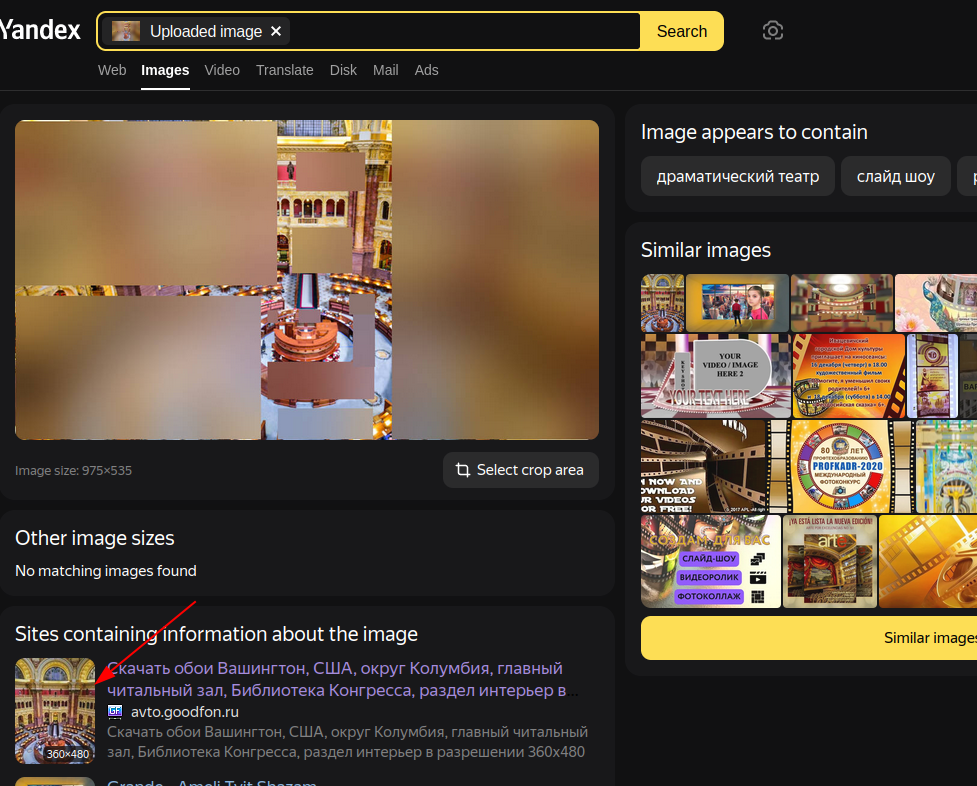
The image is distroted so let’s try to do a reverse image search.
Search the image on yendex image search, You’ll get the full image of this place and info of the place in russian language.
I was so lazy to translate, so I did google image search the full image I got from the yandex results. The place in this image is Library of Congress.
Flag: flag{LIBRARY_OF_CONGRESS}
Disguised Source Control
Pts: 200
The AI has started hiding public repositories to hide its secrets however there is still a way to access them, put your investigative skills to the test by uncovering hidden secrets within a GitHub repository using some clever Git maneuvers.
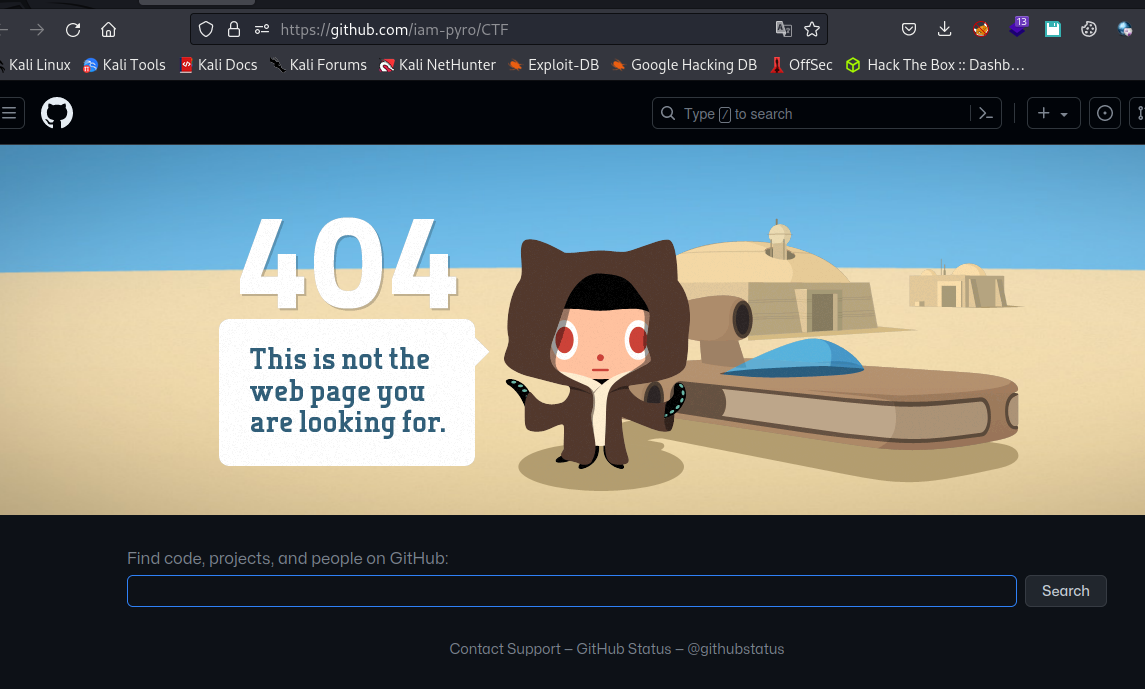
This is a very interesting challenge and will require some Git skills. When you first visit the repo URL, you’ll encounter a 404 error page. Perhaps the repo has been deleted or is private.
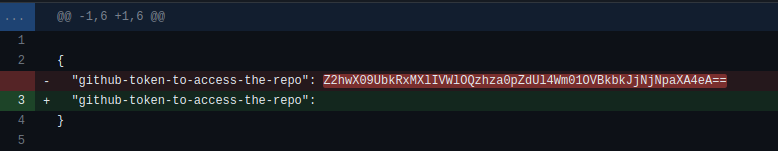
So I search the user’s profile where I found this repo Git-Tutorial, there is a commit in front of our eyes indicating that the user removed something. when I opend this commit I found a deleted github token which is encoded in base64 encoding.
Deleted github token:
{
"github-token-to-access-the-repo": Z2hwX09UbkRxMXlIVWlOQzhza0pZdUl4Wm01OVBkbkJjNjNpaXA4eA==
"github-token-to-access-the-repo":
}
You can decode this base64 encoding with kali linux’s built in tool base64 with below command or using this website base64decode.org online.
command:
echo "Z2hwX09UbkRxMXlIVWlOQzhza0pZdUl4Wm01OVBkbkJjNjNpaXA4eA=="|base64 -d
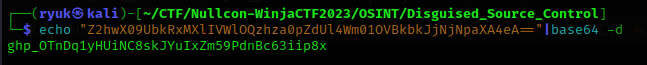
github token: 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
Now we have the secret github token, so let’s try to clone the private repo using our treditional method git clone repo_url using this token.
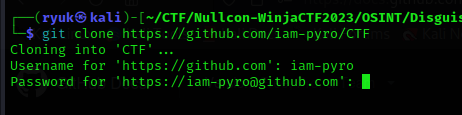
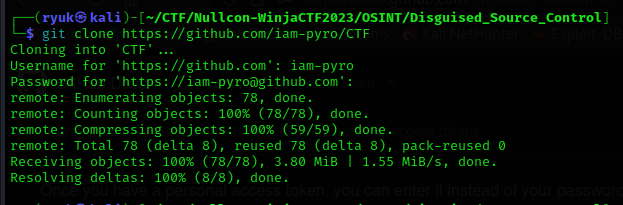
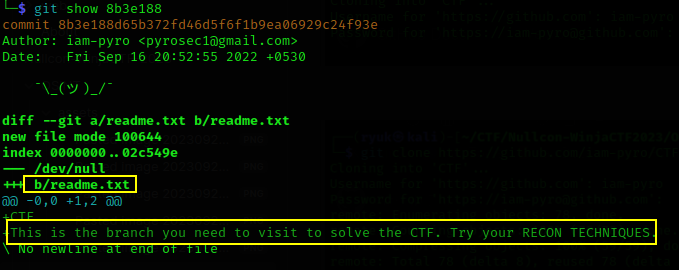
By looking into git logs, I found a merge commit from another branch to the main branch. The file contents indicate that we need to access that branch to solve the CTF.
But there is no other branch other than main locally, to view remote branches you can use git branch -r it will list all the available remote branch.
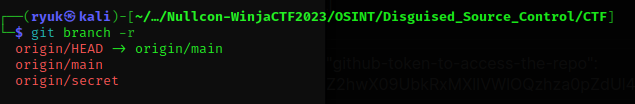
As you are able to see there is an another branch origin/secret, to clone this branch use git clone -b secret https://github.com/iam-pyro/CTF.
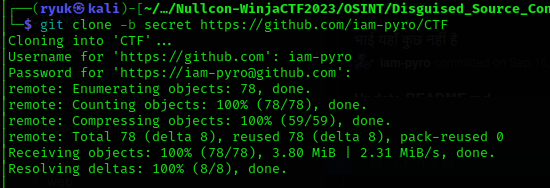
This branch contains source code for a web application, After analyzing the cource code I found the first half portion of our flag in this file src/components/drawer-item.svelte.
src/components/drawer-item.svelte:
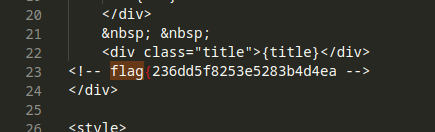
After finishing the source code, I didn’t find the other part of the flag. So, I moved on to the next step and started looking at the commit logs. There, I found the second portion of the flag in a commit message.
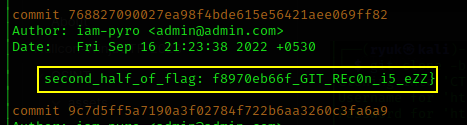
Flag: flag{236dd5f8253e5283b4d4eaf8970eb66f_GIT_REc0n_i5_eZZ}